
The 2024 Snowflake breach wasn't a sophisticated hack. There was no zero-day exploit, no advanced malware, no breach of Snowflake's infrastructure. Attackers simply logged in with stolen passwords.
That's what makes it so alarming.
Over 165 organizations were compromised, more than 500 million individuals had their data exposed, and companies like AT&T, Ticketmaster, Santander, and Advance Auto Parts found themselves in headlines for all the wrong reasons. AT&T alone lost call records for nearly all of its wireless customers and reportedly paid a $370,000 ransom.
The root cause?
Credentials stolen by infostealer malware, some dating back to 2020, that were never rotated. Accounts that lacked multi-factor authentication. And a shared responsibility model that left security gaps wide open.
Here's what happened, why it matters, and how to make sure your organization isn't the next victim.
The Snowflake breach didn't start with Snowflake. It started years earlier when employees at various organizations were infected with infostealer malware like VIDAR, RISEPRO, REDLINE, LUMMA, and METASTEALER. These infostealers harvested credentials from browsers, password managers, and applications, then uploaded them to criminal marketplaces.
Among the stolen credentials were usernames and passwords for Snowflake accounts. Over 80% of the compromised accounts had prior credential exposure, according to Mandiant's investigation. The credentials sat in dark web forums and Telegram channels, waiting for someone to use them.
In spring 2024, a threat group tracked as UNC5537 (also associated with ShinyHunters) recognized the opportunity. Snowflake is a cloud data warehousing platform used by thousands of enterprises to store and analyze massive datasets. Access to a single Snowflake tenant could mean access to terabytes of sensitive customer data.
The attackers didn't need to find vulnerabilities. They simply tested stolen credentials against Snowflake login portals. When the credentials worked (and they often did, because the passwords hadn't been changed), the attackers logged in.
The critical enabler: the compromised accounts did not have multi-factor authentication enabled. A valid username and password was all it took.
Once inside, UNC5537 moved quickly. Using database management tools like DBeaver and custom Python scripts with Salesforce's Bulk API, they ran queries to export entire databases:
The attackers used VPN services (Mullvad, Private Internet Access) to mask their origins and stored exfiltrated data on cloud providers like MEGA and VPS systems from ALEXHOST in Moldova.
Snowflake became aware of suspicious activity in mid-April 2024. By May 23, they acknowledged potential unauthorized access. In collaboration with Mandiant and CrowdStrike, Snowflake notified approximately 165 potentially exposed organizations through their Victim Notification Program.
On May 30, Snowflake published detection guidance and hardening recommendations. But for many victims, the damage was already done.
The Snowflake breach hit some of the biggest names in business:
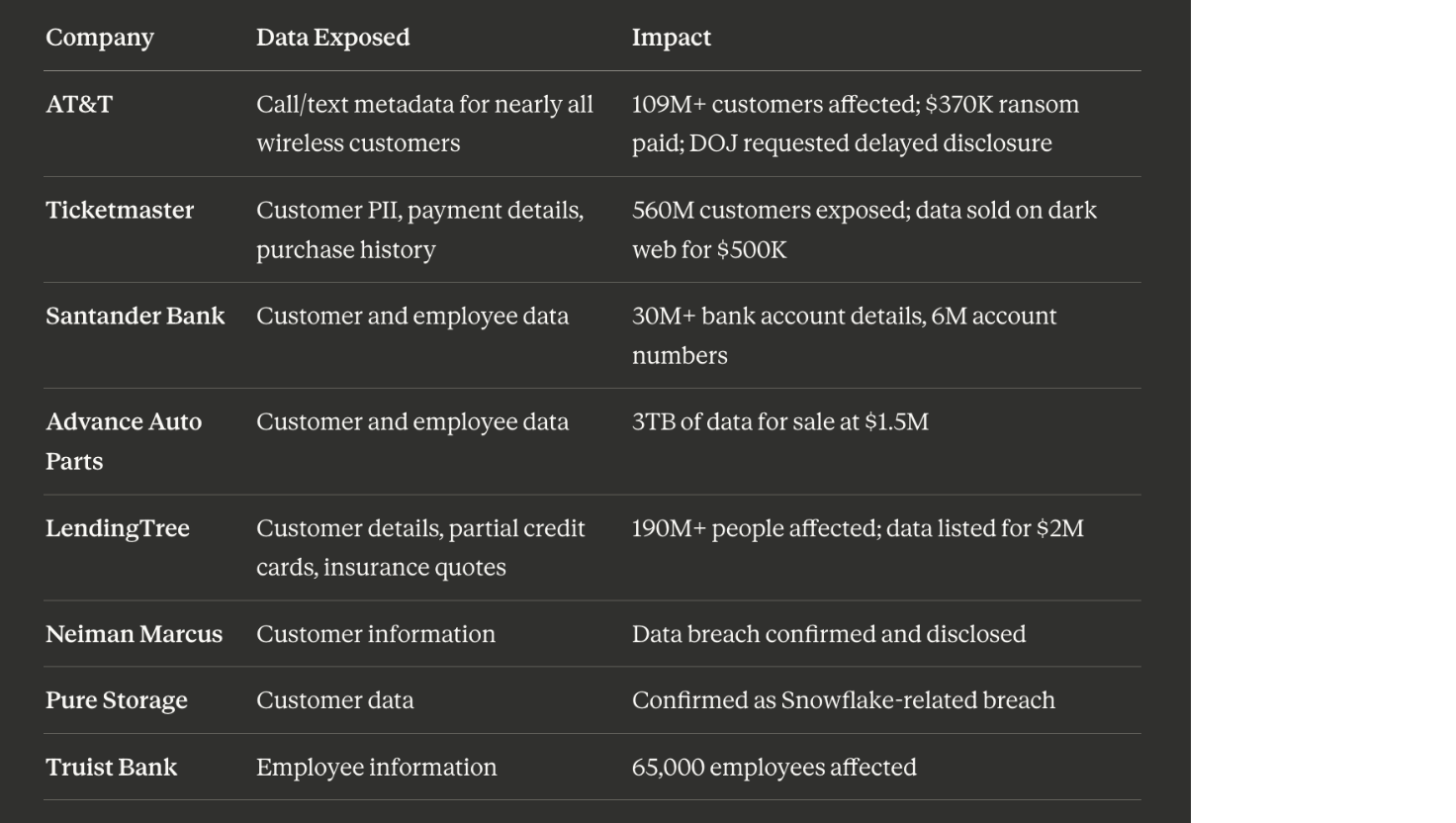
The stolen data was used for extortion. Victims received ransom demands threatening to leak or sell the information. Some paid. Others watched their data appear on criminal forums.
The Snowflake breach is a landmark event in cloud security, not because of technical sophistication, but because of its simplicity. It proved that identity attacks on cloud services can be just as devastating as traditional network intrusions, with far less effort required from attackers.
Infostealer malware is everywhere. Employees click phishing links, download infected software, or visit compromised websites. The malware silently harvests credentials and exfiltrates them to criminal infrastructure. According to Mandiant, the credentials used in the Snowflake attacks dated back as far as 2020.
If you haven't rotated passwords in years, attackers may already have them.
Over 80% of compromised Snowflake accounts lacked multi-factor authentication. This single security control would have stopped the vast majority of these attacks. Even with valid credentials, attackers couldn't have logged in without the second factor.
Snowflake offered MFA. Customers chose not to enable it.
Cloud providers operate under a shared responsibility model: the provider secures the infrastructure, and customers secure their data, identities, and configurations. Snowflake's infrastructure was never breached. But customers' failure to implement basic security controls left their data exposed.
The problem is that many organizations don't fully understand their responsibilities, or don't have visibility into whether those responsibilities are being met.
The Snowflake breach demonstrated that you don't need to breach a network to steal data. You just need credentials. In a world of cloud services and SaaS applications, identity has become the primary attack surface. Organizations that focus only on network security are missing the bigger picture.
Understanding the attacker's playbook helps inform detection and prevention.
UNC5537 didn't steal credentials themselves. They purchased or acquired them from underground markets where infostealer logs are sold. These logs contain browser-saved passwords, session cookies, and authentication tokens harvested from infected machines.
Using tools like the Snowflake Python Connector and DBeaver, attackers authenticated to victim Snowflake instances with stolen usernames and passwords. Without MFA, this was all they needed.
Mandiant observed attackers using a custom tool they called "rapeflake" (visible in connection logs) to automate the process across multiple targets.
Once authenticated, attackers used Snowflake's Bulk API to export large datasets efficiently. They queried standard Snowflake objects to enumerate available data, then executed bulk exports of valuable tables.
After exfiltrating data, attackers deleted API jobs to cover their tracks. However, Snowflake's event monitoring logs retained evidence of the access patterns, enabling forensic reconstruction.
Stolen data was advertised on cybercrime forums like BreachForums. Victims received extortion demands. Some data was sold to other criminal groups for secondary exploitation.
The Snowflake breach triggered significant legal consequences:
The litigation alleges that both Snowflake and its customers failed to implement adequate data security measures and provide timely breach notification. It's a reminder that security failures have consequences beyond the immediate breach.
This is the single most important lesson from the Snowflake breach. Multi-factor authentication would have prevented the vast majority of these compromises.
Action: Audit all cloud services for MFA enrollment. Enforce MFA at the identity provider level where possible. Don't rely on users to enable it voluntarily.
Credentials stolen in 2020 were still valid in 2024. That's a four-year window for attackers to exploit.
Action: Implement credential rotation policies. Use password managers to generate unique, complex passwords. Integrate with identity providers that support automatic rotation.
Your credentials may already be on the dark web. Proactive monitoring can alert you before attackers use them.
Action: Subscribe to credential monitoring services. Check breach databases for corporate email domains. Alert on matches and force password resets.
The Snowflake attackers operated for weeks before detection. Anomaly detection could have flagged suspicious login patterns, unusual query volumes, or bulk data exports.
Action: Enable logging and monitoring for all cloud services. Baseline normal access patterns. Alert on deviations like new IP addresses, unusual hours, or massive data transfers.
Cloud providers secure their infrastructure. You secure your data. If you don't understand where that line falls, you'll have gaps.
Action: Review the shared responsibility documentation for every cloud service you use. Map security controls to responsibilities. Verify that your controls are actually in place.
The Snowflake breach exploited exactly the blind spots Perimeters was built to eliminate: unmanaged credentials, missing MFA, and lack of visibility into cloud security posture.
Perimeters discovers every SaaS application in your environment, including shadow IT that employees have adopted without approval. You can't secure what you can't see.
Perimeters continuously monitors MFA enrollment across your SaaS applications. You'll know immediately if accounts lack multi-factor authentication, so you can enforce compliance before attackers exploit the gap.
Perimeters identifies risky identities across your SaaS ecosystem:
By governing identities proactively, you reduce the attack surface available to credential-based attacks.
Perimeters continuously audits your SaaS configurations against security best practices and compliance frameworks. Missing MFA, weak password policies, and overly permissive access controls are flagged automatically.
When Perimeters identifies a security issue, you can fix it with one click or automate remediation entirely. No more hunting through admin consoles across dozens of applications.
If your organization had been using Perimeters before the Snowflake breach, you would have known:
That visibility is the difference between being a headline and being protected.
The Snowflake breach proved that the biggest cloud security risk isn't sophisticated hackers or zero-day exploits. It's stolen passwords and missing MFA.
UNC5537 didn't need advanced techniques. They bought credentials on the dark web, logged in to accounts without multi-factor authentication, and walked away with hundreds of millions of records. The attack was simple, scalable, and devastatingly effective.
The lesson is clear: identity security is cloud security. Organizations need visibility into their SaaS environments, enforcement of security controls like MFA, and continuous monitoring for credential exposure and anomalous access.
The next credential-based attack is already being planned. Your stolen credentials may already be for sale. The only question is whether you'll know before the attackers use them.
Ready to secure your SaaS environment?
See how Perimeters discovers and protects your cloud applications →
The Snowflake breach was a 2024 cyberattack where threat actors used stolen credentials to access over 165 organizations' Snowflake cloud data warehouses. Attackers exfiltrated data affecting 500+ million individuals from companies including AT&T, Ticketmaster, and Santander.
No. Snowflake's core infrastructure was not compromised. Attackers used credentials stolen via infostealer malware to log in to customer accounts that lacked multi-factor authentication.
The attack was attributed to UNC5537 (also associated with ShinyHunters). Two individuals have been arrested: Connor Riley Moucka in Canada and John Erin Binns in Turkey.
