
In August 2025, a single compromised integration turned into one of the largest SaaS supply chain breaches in history. The Salesloft Drift breach affected over 700 organizations, including Cloudflare, Palo Alto Networks, Proofpoint, and Zscaler, exposing sensitive CRM data, credentials, and API keys through stolen OAuth tokens.
This wasn't a sophisticated zero-day exploit. It was a textbook example of what happens when trusted third-party integrations go unmonitored.
Here's what happened, who was affected, and most importantly, how to protect your organization from the next OAuth-based attack.
The breach unfolded in stages over several months, with the actual data exfiltration occurring in a rapid 10-day window.
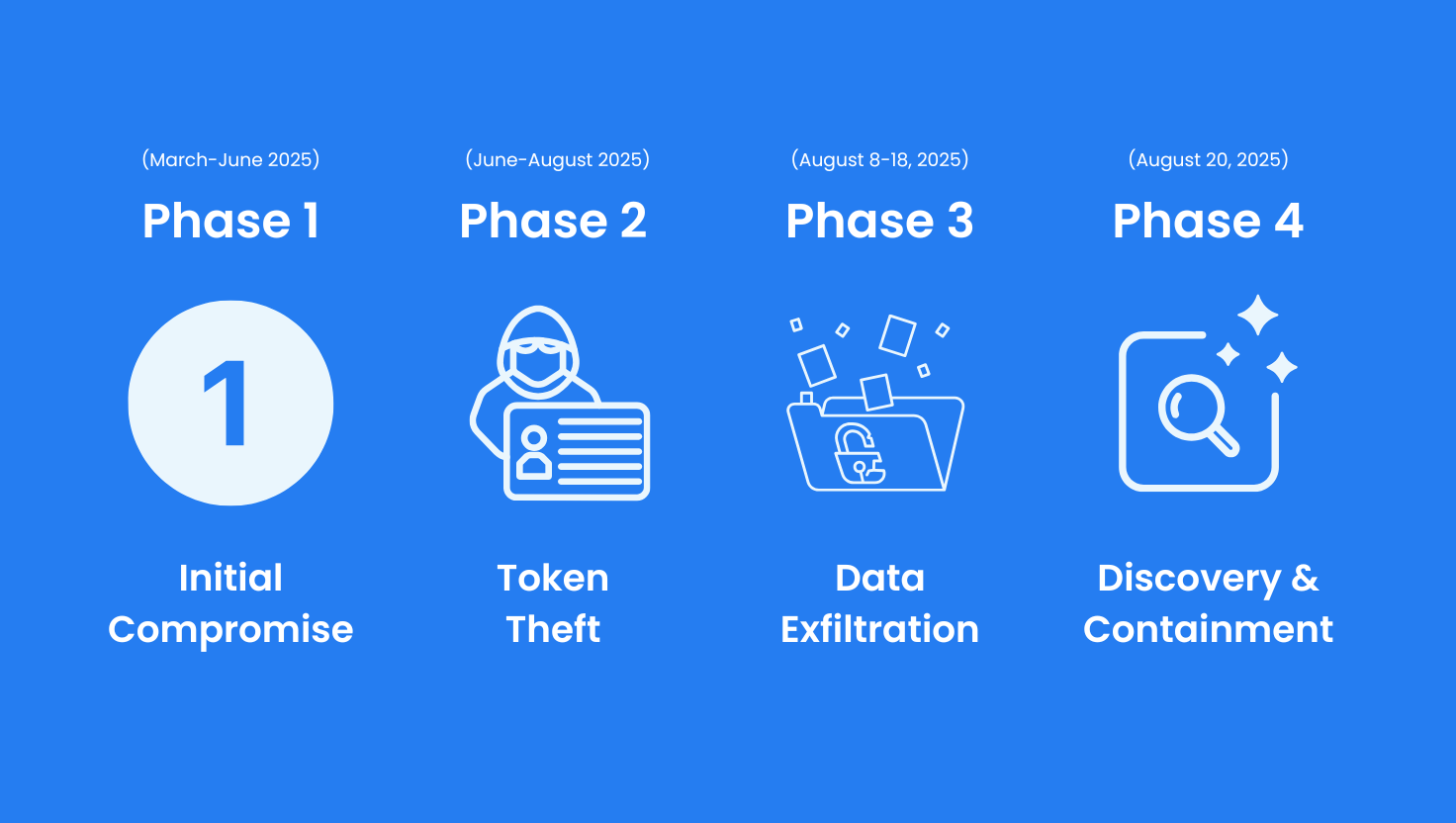
Attackers first gained access to Salesloft's GitHub account. From there, they downloaded code repositories, created a guest user for persistence, and conducted reconnaissance across both Salesloft and Drift environments.
The attackers pivoted into Drift's AWS environment, where they extracted OAuth tokens and refresh tokens tied to customer integrations. These tokens are the keys that allow Drift to access connected platforms like Salesforce, Google Workspace, and Slack on behalf of customers.
Armed with stolen OAuth credentials, the threat actor (tracked as UNC6395 by Google Threat Intelligence and Mandiant) systematically queried Salesforce instances across 700+ organizations. Using automated Python scripts and Salesforce's Bulk API, they exported massive volumes of data including:
Salesforce and Salesloft disabled all Drift integrations globally, halting the attack but causing widespread service disruption. Customer notifications began rolling out between August 26-29.
The Salesloft Drift breach isn't just another data incident. It's a wake-up call about a fundamental security gap in modern SaaS environments.
Every time an employee clicks "Accept" on an OAuth consent screen, they're granting that application ongoing access to your systems. Unlike passwords, OAuth tokens:
In this breach, the attackers didn't need to compromise Salesforce directly. They simply impersonated the trusted Drift application using stolen tokens, and Salesforce had no way to distinguish malicious queries from legitimate ones.
What made this breach so devastating was scale. A single point of compromise (Drift's OAuth tokens) gave attackers access to every Salesforce instance connected to Drift. This is the nature of SaaS supply chain risk: one vendor's security failure becomes every customer's problem.
Victims included some of the most security-conscious organizations in the world. If Cloudflare, Palo Alto Networks, and Zscaler couldn't prevent this, what chance does the average enterprise have without dedicated SaaS security tooling?
The confirmed victim list reads like a who's who of enterprise technology:

The common thread: all were using legitimate, sanctioned integrations with a trusted vendor. Traditional security tools saw nothing unusual until it was too late.
Understanding the attacker's methods helps inform detection and prevention strategies.
UNC6395 used Python scripts with asynchronous libraries (aiohttp) to maximize exfiltration speed. They executed Salesforce Object Query Language (SOQL) queries to systematically export:
SELECT Id, Name, Email FROM Contact
SELECT Id, Subject, Description FROM Case
SELECT Id, Amount, StageName FROM Opportunity
The attackers weren't just after contact lists. They were hunting for secrets. Support cases often contain embedded credentials shared during troubleshooting. AWS keys, database passwords, and API tokens buried in case descriptions became secondary compromise vectors.
After bulk exports, UNC6395 deleted API jobs to conceal their activity. While this removed immediate evidence, Salesforce event monitoring logs still captured the access patterns. This is a reminder that comprehensive logging is essential.
OAuth tokens grant persistent, often privileged access to your most sensitive systems. Yet most organizations have no inventory of active tokens, no visibility into their permissions, and no process for regular rotation.
Action: Implement continuous monitoring of OAuth grants across your SaaS environment. Know which applications have access to what data, and revoke tokens that are unused, overprivileged, or connected to risky vendors.
The principle of least privilege applies to application integrations, not just human users. Drift didn't need access to Opportunities or Cases to power a chat widget, but it had it anyway.
Action: Review the OAuth scopes granted to every connected application. Reduce permissions to the minimum required for functionality. If a vendor can't operate with restricted scopes, that's a red flag.
Bulk data exports from a chat application should trigger immediate alerts. The 10-day window attackers had was far too long. Earlier detection could have limited the damage.
Action: Baseline normal API activity for each integration and alert on deviations. Unusual query patterns, bulk exports, and access from new IP ranges are all indicators of compromise.
Your security is only as strong as your weakest integration. Salesloft and Drift were trusted vendors, but their compromise became every customer's breach.
Action: Evaluate the security posture of SaaS vendors before connecting them to sensitive systems. Require SOC 2 reports, assess their integration architecture, and monitor for vendor security incidents.
When (not if) an OAuth-based breach occurs, your team needs to move fast. Identifying affected tokens, revoking access, and assessing data exposure requires visibility most organizations don't have.
Action: Build playbooks specifically for SaaS integration compromises. Ensure you can quickly identify all tokens associated with a compromised vendor and revoke them across your environment.
The Salesloft Drift breach exploited exactly the blind spot Perimeters was built to close.
Perimeters automatically discovers every OAuth-connected application in your environment, including Shadow SaaS applications employees have authorized without IT approval. You get complete visibility into:
Not all OAuth grants are equal. Perimeters analyzes each connection's permissions, vendor security posture, and usage patterns to surface the highest-risk integrations first. Applications with broad data access from vendors with weak security controls get flagged immediately.
When you identify a risky or unnecessary OAuth connection, Perimeters lets you revoke access with one click, or automatically based on policies you define. No more hunting through individual application admin consoles.
Perimeters monitors for suspicious OAuth activity including:
If Drift had been connected through an environment monitored by Perimeters, the anomalous bulk queries would have triggered immediate alerts, potentially cutting the breach window from 10 days to minutes.
The Salesloft Drift breach is a stark reminder that every SaaS integration comes with security debt. The convenience of connected applications has a cost, and for 700+ organizations, that bill came due in August 2025.
The attackers didn't find a vulnerability in Salesforce. They didn't crack encryption or bypass MFA. They simply abused the trust organizations placed in their third-party integrations.
The lesson is clear: OAuth tokens are credentials, and they need to be managed as such. Organizations need continuous visibility into their SaaS integrations, the ability to assess risk, and the tools to respond quickly when a trusted vendor is compromised.
The next OAuth-based supply chain attack is already being planned. The question is whether your organization will see it coming.
Ready to close your OAuth blind spot?
See how Perimeters discovers and secures your SaaS integrations.
Attackers first compromised Salesloft's GitHub account, then pivoted to Drift's AWS environment where they stole OAuth tokens. These tokens allowed them to impersonate the legitimate Drift application and query Salesforce instances without triggering security alerts.
Exposed data varied by organization but commonly included Salesforce contacts, accounts, opportunities, and support cases. More critically, attackers extracted API keys, cloud credentials, and passwords embedded in support tickets.
Key protections include: maintaining an inventory of all OAuth-connected applications, auditing permission scopes, monitoring for anomalous API activity, implementing vendor risk management, and using SaaS security tools like Perimeters.io to automate discovery and remediation.
If your organization used Drift integrations with Salesforce between August 8-20, 2025, you may have been impacted. Check Salesloft's trust portal and review Salesforce audit logs for unusual activity during that period.
