
Grip Security built its reputation on identity-centric SaaS discovery. But Grip isn't the only game in town.
The SaaS security market has exploded over the past two years, with competitors tackling the problem from different angles: some focus on configuration management, others on threat detection, and still others on user-centric remediation.
If you're evaluating Grip Security or looking for alternatives, this guide covers nine competitors worth considering. We've organized them by primary strength so you can quickly find options that match your priorities.
Full disclosure: Perimeters.io is on this list. We built our platform because we saw gaps in how existing tools approach SaaS security.
We will be honest about where we excel and where others might be a better fit.
Without further ado, here are the 9 best Grip security competitors for SaaS security.

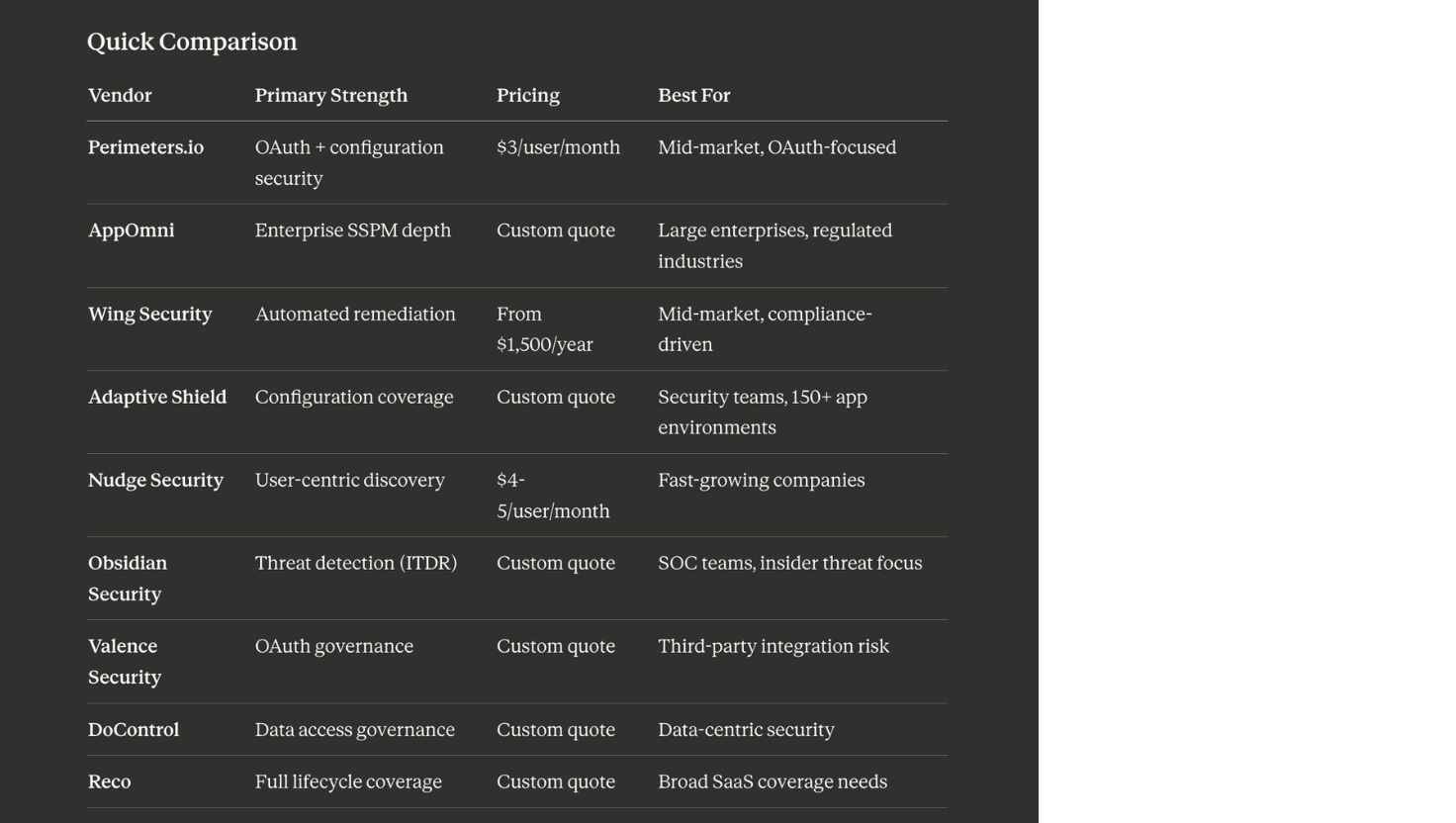
Primary strength: Overall best Grip Security competitor. OAuth security and configuration management with transparent pricing
What sets it apart:
Perimeters was built around a simple thesis: the next wave of SaaS breaches will come through application integrations, not user credentials. The Salesloft Drift attack proved this when stolen OAuth tokens compromised 700+ organizations. The Snowflake breach showed what happens when basic configurations like MFA go unenforced.
Perimeters takes an application-centric approach rather than identity-centric. We connect directly to your SaaS platforms via API and examine configurations, permissions, and OAuth grants from the inside out. This gives us visibility into what applications can actually do, not just who's using them.
Key capabilities:
Pricing: $3 per active user per month.
Deployment: Minutes via API connection. No agents, no browser extensions.
Best for: Organizations where OAuth risk and configuration security are primary concerns. Mid-market companies that want enterprise capabilities without enterprise procurement and pricing.
Limitations: Less focused on threat detection, like many other SaaS security vendors.
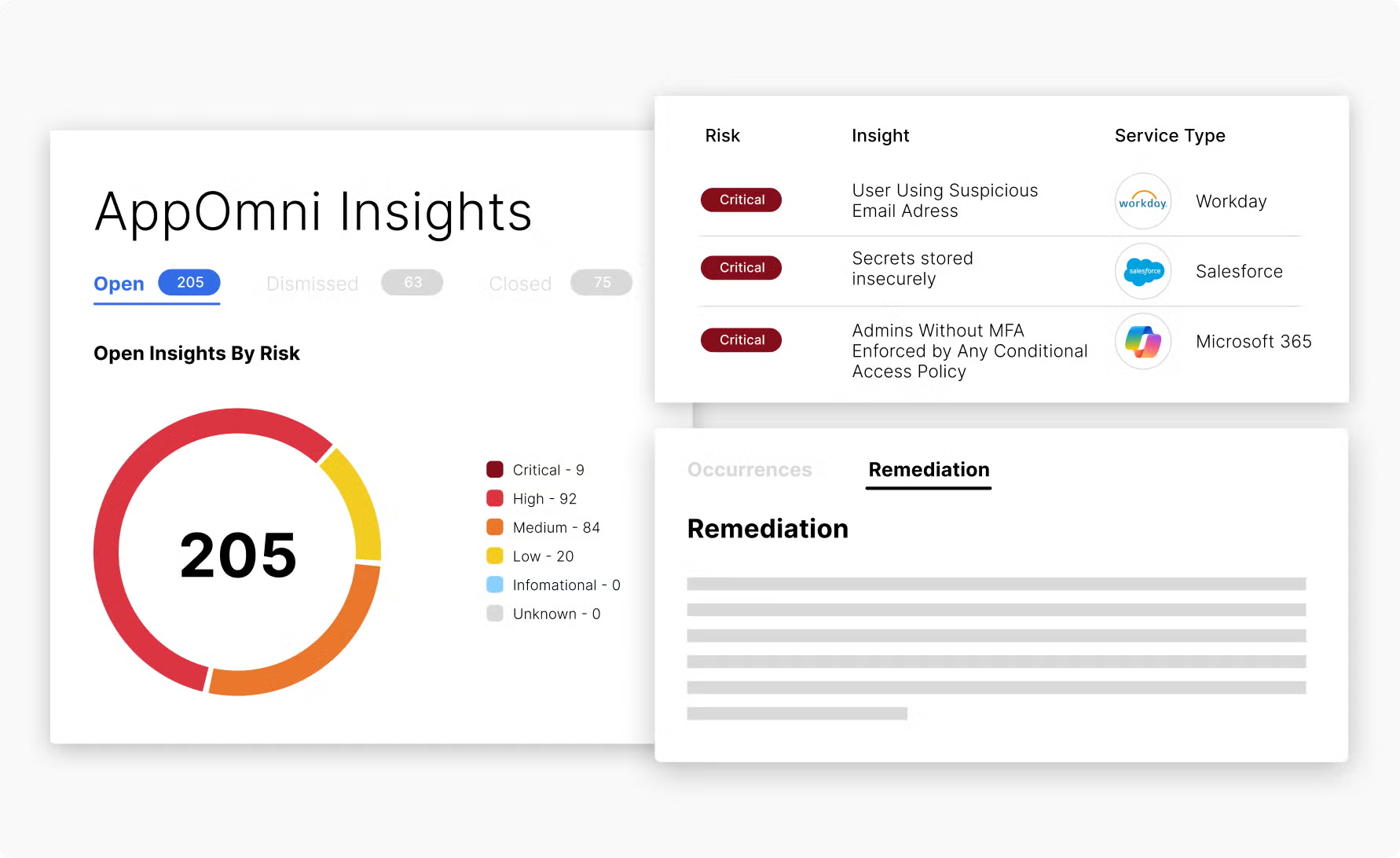
Primary strength: Deep enterprise SSPM with extensive app coverage
What sets it apart:
AppOmni is the incumbent in enterprise SSPM. They've built deep integrations with business-critical applications like Salesforce, ServiceNow, and Workday, providing configuration visibility that goes beyond surface-level checks.
Their strength is depth over breadth. Where some platforms offer shallow coverage across many apps, AppOmni provides granular configuration analysis for the applications that matter most to large enterprises.
Key capabilities:
Pricing: Custom quotes. Per-application or per-user licensing options. Industry estimates suggest enterprise-tier pricing.
Best for: Large enterprises with complex Salesforce, ServiceNow, or Workday deployments. Organizations in regulated industries (finance, healthcare) that need deep compliance controls.
Limitations: Enterprise pricing and sales process. May be overkill for mid-market organizations or those without complex enterprise SaaS deployments.

Primary strength: Automated remediation with accessible pricing
What sets it apart:
Wing Security has taken a product-led approach to SSPM, offering a free tier and accessible pricing that makes SaaS security available to smaller organizations. Their focus on automation means security teams can "set and forget" many common remediation tasks.
Wing's discovery uses multiple methods: OAuth integration, email scanning, and endpoint scanning. They maintain a database of 280,000+ SaaS applications for risk assessment.
Key capabilities:
Pricing: Essential SSPM starts at $1,500/year for entire organization. Enterprise tiers available. Free discovery tier.
Deployment: API-based, connects to Google Workspace or Microsoft 365 in minutes.
Best for: Mid-market organizations that want automation without enterprise pricing. Teams that need to demonstrate compliance quickly. Organizations just starting their SaaS security journey.
Limitations: Less deep on individual application configurations compared to AppOmni. Enterprise features require higher tiers.
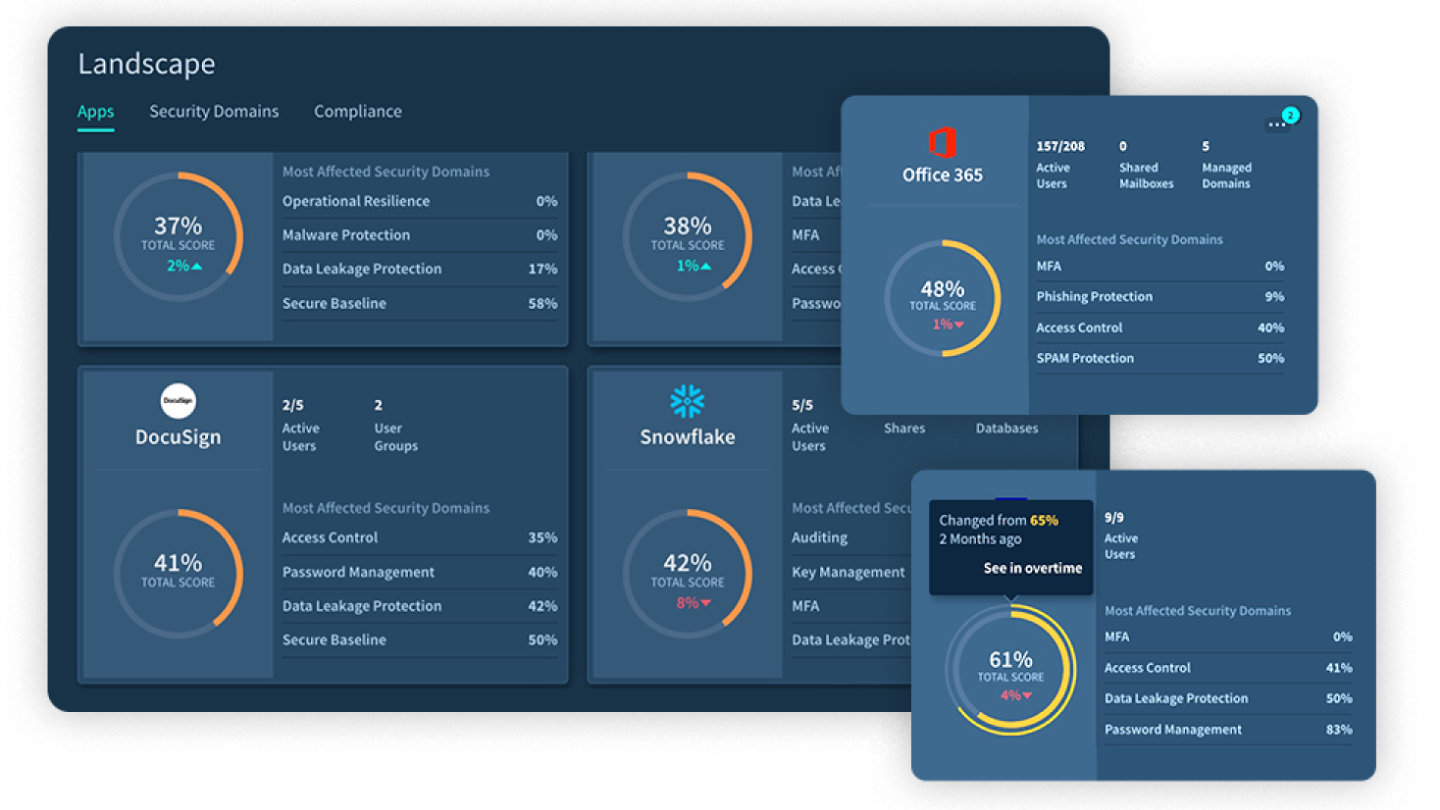
Primary strength: Broadest configuration coverage with 150+ integrations
What sets it apart:
Adaptive Shield (now part of CrowdStrike) positions itself on integration breadth. With 150+ SaaS application integrations, they offer configuration monitoring across more applications than most competitors. Their acquisition by CrowdStrike adds enterprise credibility and potential for deeper endpoint integration.
Key capabilities:
Pricing: Tiered enterprise pricing. Custom quotes.
Best for: Security teams managing large, diverse SaaS environments. Organizations already using CrowdStrike who want consolidated visibility. Enterprises that prioritize configuration coverage breadth.
Limitations: CrowdStrike acquisition may mean changes to standalone availability. Less focused on SaaS discovery compared to identity-centric platforms.
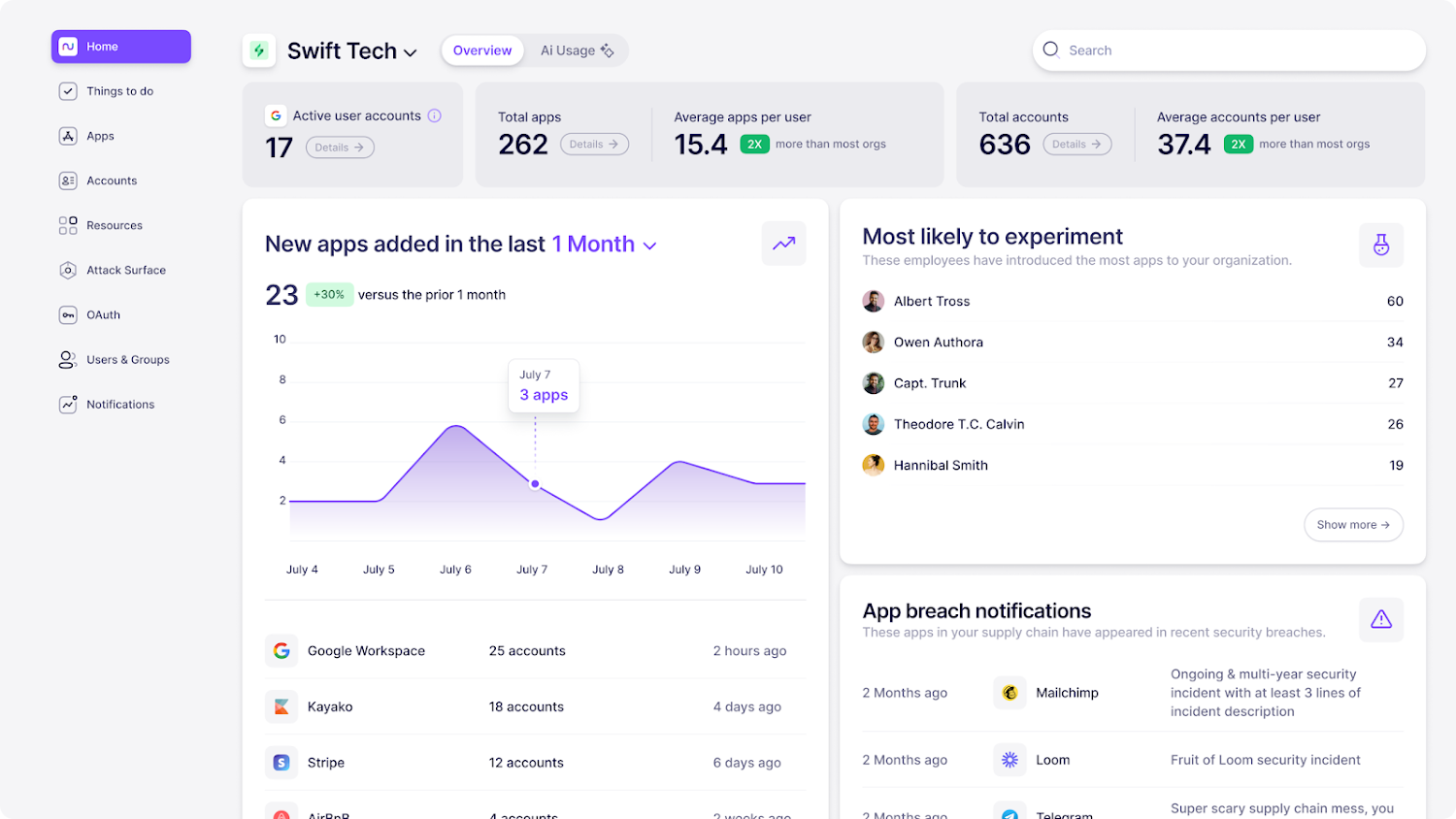
Primary strength: User-centric discovery with behavioral nudges
What sets it apart:
Nudge Security takes a philosophically different approach. Rather than blocking or restricting SaaS usage, they "nudge" users toward secure behaviors. Their patented discovery method finds shadow SaaS without requiring prior knowledge of which apps to monitor.
The platform emphasizes collaboration between security teams and employees, making security a shared responsibility rather than an IT mandate.
Key capabilities:
Pricing: $4-5 per active user per month. 14-day free trial.
Deployment: Single integration. No agents, endpoints, or browser extensions.
Best for: Fast-growing organizations that want to enable SaaS adoption while managing risk. Companies that value user experience alongside security. Teams that need comprehensive shadow IT discovery.
Limitations: Less focused on deep configuration remediation. The "nudge" approach requires cultural buy-in from employees. Some reviewers note they're still developing features that larger competitors offer.
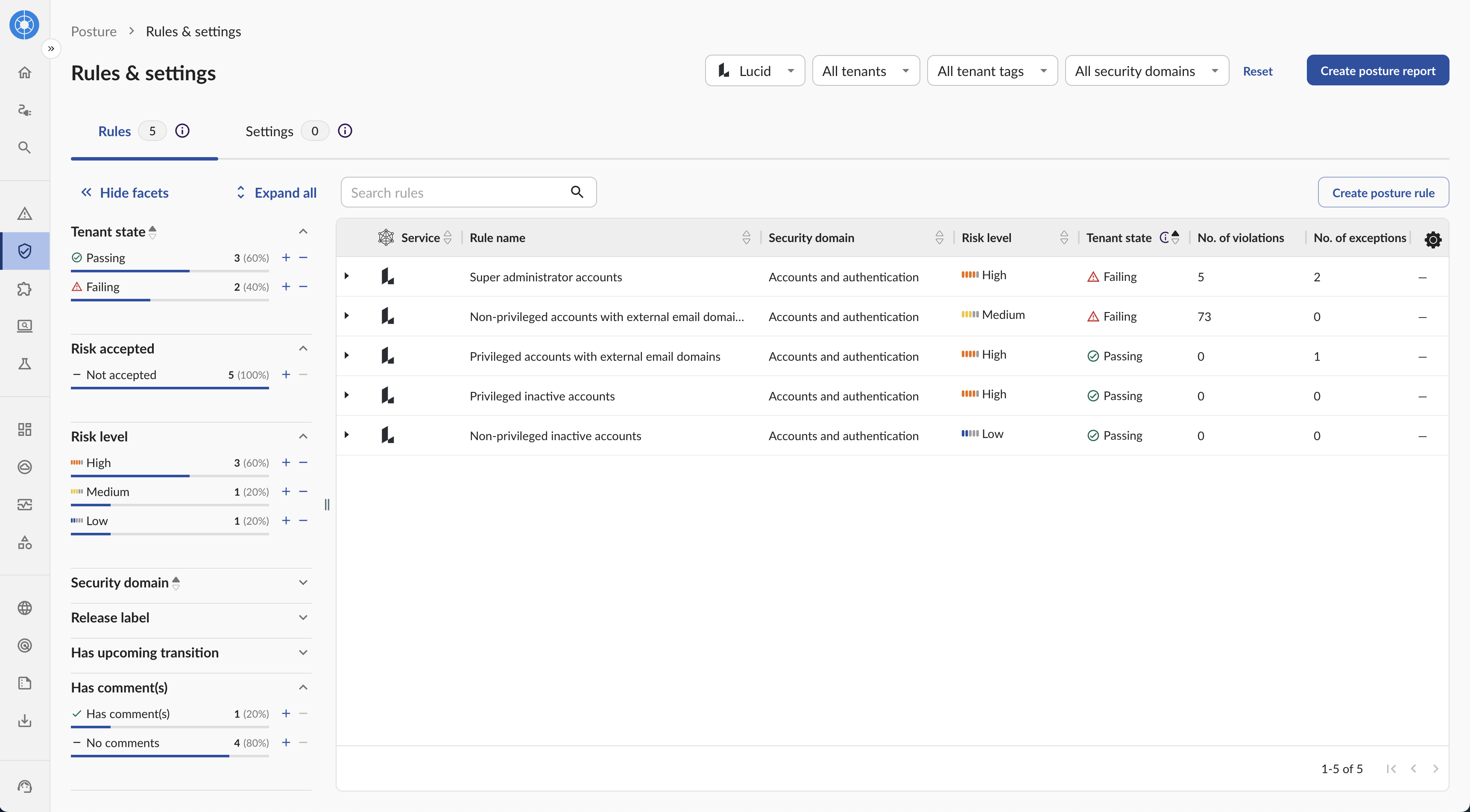
Primary strength: Threat detection and insider risk
What sets it apart:
Obsidian Security combines SSPM with User and Entity Behavior Analytics (UEBA) to detect active threats within SaaS applications. While most SSPM platforms focus on prevention (finding misconfigurations before they're exploited), Obsidian adds detection capabilities for threats already in progress.
This makes Obsidian particularly strong for SOC teams that need to investigate suspicious activity, not just harden configurations.
Key capabilities:
Pricing: Custom quotes.
Best for: Organizations with mature SOC operations. Companies concerned about insider threats. Security teams that need detection capabilities alongside posture management.
Limitations: Less comprehensive on SaaS discovery compared to dedicated discovery platforms. Browser-based shadow app detection may be limited to Chrome. Higher complexity for teams without dedicated SOC resources.
Primary strength: OAuth and third-party integration governance
What sets it apart:
Valence Security focuses specifically on the risks created by SaaS-to-SaaS integrations. As organizations connect more applications via OAuth and API integrations, Valence provides visibility into this web of permissions and automates governance of third-party access.
Their approach includes automated third-party app reviews and one-click remediation for OAuth permissions.
Key capabilities:
Pricing: Custom quotes.
Best for: Organizations with extensive third-party SaaS integrations. Companies concerned about OAuth permission sprawl. Security teams that want to involve business users in remediation decisions.
Limitations: Newer entrant compared to established players. Custom pricing requires sales engagement.

Primary strength: Data access governance
What sets it apart:
DoControl approaches SaaS security from a data-centric perspective. Rather than focusing primarily on users or configurations, they emphasize understanding and controlling who has access to sensitive data within SaaS applications.
Their zero-trust enforcement capabilities help organizations implement least-privilege access across SaaS environments.
Key capabilities:
Pricing: Custom quotes.
Best for: Organizations where data access control is the primary concern. Companies with sensitive data in Google Workspace or Microsoft 365. Security teams implementing zero-trust architecture.
Limitations: Reviewers note complex initial setup for mid-sized teams. Less focused on broader SaaS discovery.
Primary strength: Full lifecycle SaaS security with AI governance
What sets it apart:
Reco positions itself as a comprehensive SaaS security platform covering the entire lifecycle: discovery, posture management, identity governance, and threat detection. They've invested heavily in AI governance capabilities as organizations adopt generative AI tools.
Their contextual, graph-based approach to identity management provides unified visibility across SaaS platforms.
Key capabilities:
Pricing: Custom quotes.
Best for: Organizations seeking a single platform for multiple SaaS security needs. Companies prioritizing AI governance alongside traditional SaaS security. Enterprises that want broad coverage without multiple point solutions.
Limitations: Broader platforms can mean less depth in specific areas. Custom pricing and enterprise sales process.
Consider: Perimeters.io, AppOmni, or Adaptive Shield
These platforms focus on finding and fixing misconfigurations before they're exploited. The Snowflake breach demonstrated why this matters: 80%+ of compromised accounts simply lacked MFA enforcement.
Consider: Perimeters.io or Valence Security
Both platforms treat OAuth grants as first-class security objects, analyzing permissions, vendor risk, and usage patterns. The Salesloft Drift breach showed how trusted integrations can become attack vectors.
Consider: Perimeters.io, Nudge Security, Wing Security, or Grip Security
These platforms excel at finding SaaS applications you didn't know existed. Nudge and Wing offer accessible pricing; Grip provides historical visibility and identity-centric analysis.
Consider: Obsidian Security or Reco
Both add detection capabilities alongside posture management, helping SOC teams identify and respond to threats already in progress.
Consider: Perimeters.io ($3/user/month)
Perimeters is undoubtedly the most budget-friendly SaaS security option on the market in 2026 compared to solutions like Appomni, Reco, and others.
Consider: AppOmni, Adaptive Shield, or Reco
These platforms cater to enterprise-scale deployments with deep integrations and comprehensive compliance capabilities.
The SaaS security market is maturing rapidly. Two years ago, most organizations had no dedicated SaaS security tooling. Today, there are dozens of vendors with different approaches, strengths, and pricing models.
Grip Security carved out a real position with identity-centric discovery and automated offboarding. But depending on your priorities, configuration security, OAuth governance, threat detection, or simply budget constraints, one of these alternatives may be a better fit.
The best way to decide? Run actual evaluations. Most vendors offer free trials or assessments. See which platform finds issues you didn't know existed, and which makes remediation practical rather than theoretical.
Want to see how Perimeters.io compares?
Get a demo and see the platform work in real-time.
Grip Security is a SaaS identity risk management platform that discovers shadow SaaS applications, maps identity-to-application relationships, and automates offboarding for unfederated applications. It uses email flow analysis, browser activity, and IdP data to provide visibility into SaaS usage across an organization.
The main Grip Security competitors include AppOmni, Adaptive Shield (CrowdStrike), Wing Security, Nudge Security, Obsidian Security, Valence Security, DoControl, Reco, and Perimeters.io. Each takes a different approach to SaaS security, focusing on configuration management, threat detection, or identity governance.
Grip Security uses custom pricing based on user volume. They do not publish rates, and pricing requires engagement with their sales team. Industry analysts suggest enterprise-tier pricing typical of the SSPM/SIRM category.
Perimeters.io offers transparent per-user pricing at $3/user/month - which is likely the most budget-friendly option you will find when searching for Grip security alternatives.
