
The SaaS security landscape shifted dramatically when CrowdStrike acquired Adaptive Shield in late 2024 for approximately $300 million. While Adaptive Shield - now rebranded as CrowdStrike Falcon Shield - brought solid misconfiguration monitoring capabilities, the acquisition has left many organizations reconsidering their options.
Whether you're concerned about vendor lock-in with CrowdStrike's expanding platform, frustrated by opaque enterprise pricing, or simply need a solution that delivers faster time-to-value, this guide covers the best Adaptive Shield alternatives for 2026.
The CrowdStrike acquisition changed the calculus for many Adaptive Shield customers. Here's what's driving teams to evaluate alternatives:
Post-acquisition uncertainty. Integration into CrowdStrike's Falcon platform means Adaptive Shield's roadmap now serves CrowdStrike's broader strategy - not necessarily the needs of standalone SSPM buyers. Organizations that don't want the full CrowdStrike suite are left wondering about long-term support and pricing.
Opaque, enterprise-only pricing. Adaptive Shield has never published pricing tiers. Every prospect must contact sales for a custom quote, making budget planning difficult and creating leverage imbalances during negotiations. Analysts note this "quote-only" approach leads to unpredictable costs that often exceed competitors with transparent pricing.
Manual remediation burden. While Adaptive Shield excels at identifying misconfigurations, actually fixing issues still requires significant manual effort. Users report that the platform alerts you to problems but doesn't automate the resolution - leaving security teams with a growing backlog of findings they lack time to address.
Limited application coverage. Despite claims of 150+ integrations, users consistently report gaps. G2 reviewers note "the coverage of applications they cover seems to be limited," forcing organizations to maintain blind spots or supplement with additional tools.
Declining market position. According to PeerSpot data, Adaptive Shield's mindshare in the SSPM category dropped from 12.1% to 8.4% year-over-year - a significant decline that suggests customers are actively exploring alternatives.
When evaluating SSPM replacements, prioritize these capabilities:
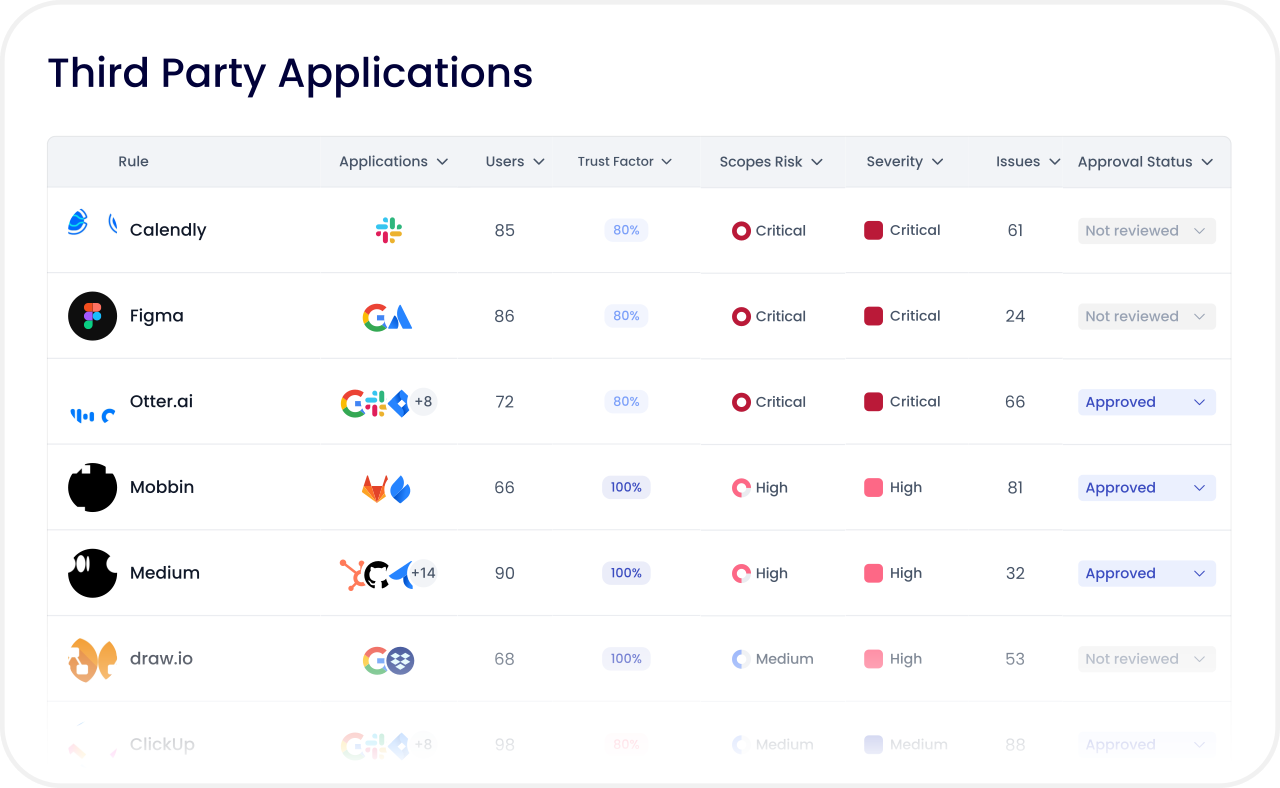
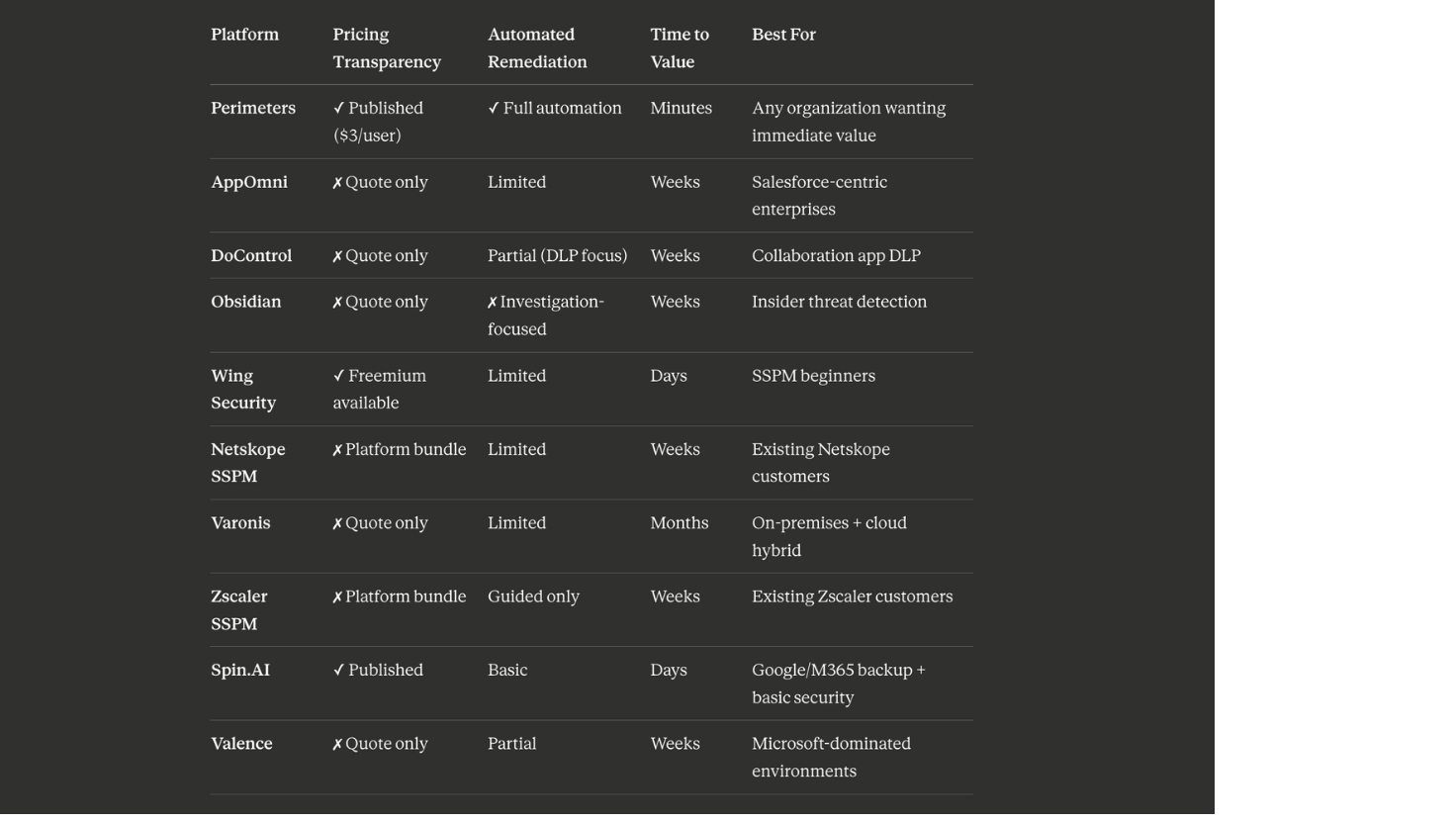
Best for: Automated SaaS security with transparent pricing and immediate value
Perimeters delivers what Adaptive Shield promises but rarely achieves: comprehensive SaaS security that works from day one, with pricing you can actually plan around.
Where Adaptive Shield identifies problems and leaves you to fix them manually, Perimeters automates the entire remediation lifecycle. Where Adaptive Shield requires custom quotes and lengthy sales cycles, Perimeters publishes simple per-user pricing. Where Adaptive Shield takes weeks to deploy, Perimeters delivers full visibility in minutes.
Key strengths:
What customers say:
"Perimeters gives us a central point of control, providing clear findings and remediation tools to save time and reduce confusion."
"With Perimeters I can spend a few minutes at a time taking care of well-defined issues with all the information in one place, saving significant time when it comes to auditing."
Pricing: $3 per active user per month - transparent, predictable, no surprises.
Best suited for: Security teams of any size who want comprehensive SSPM without enterprise complexity, opaque pricing, or manual remediation burdens.
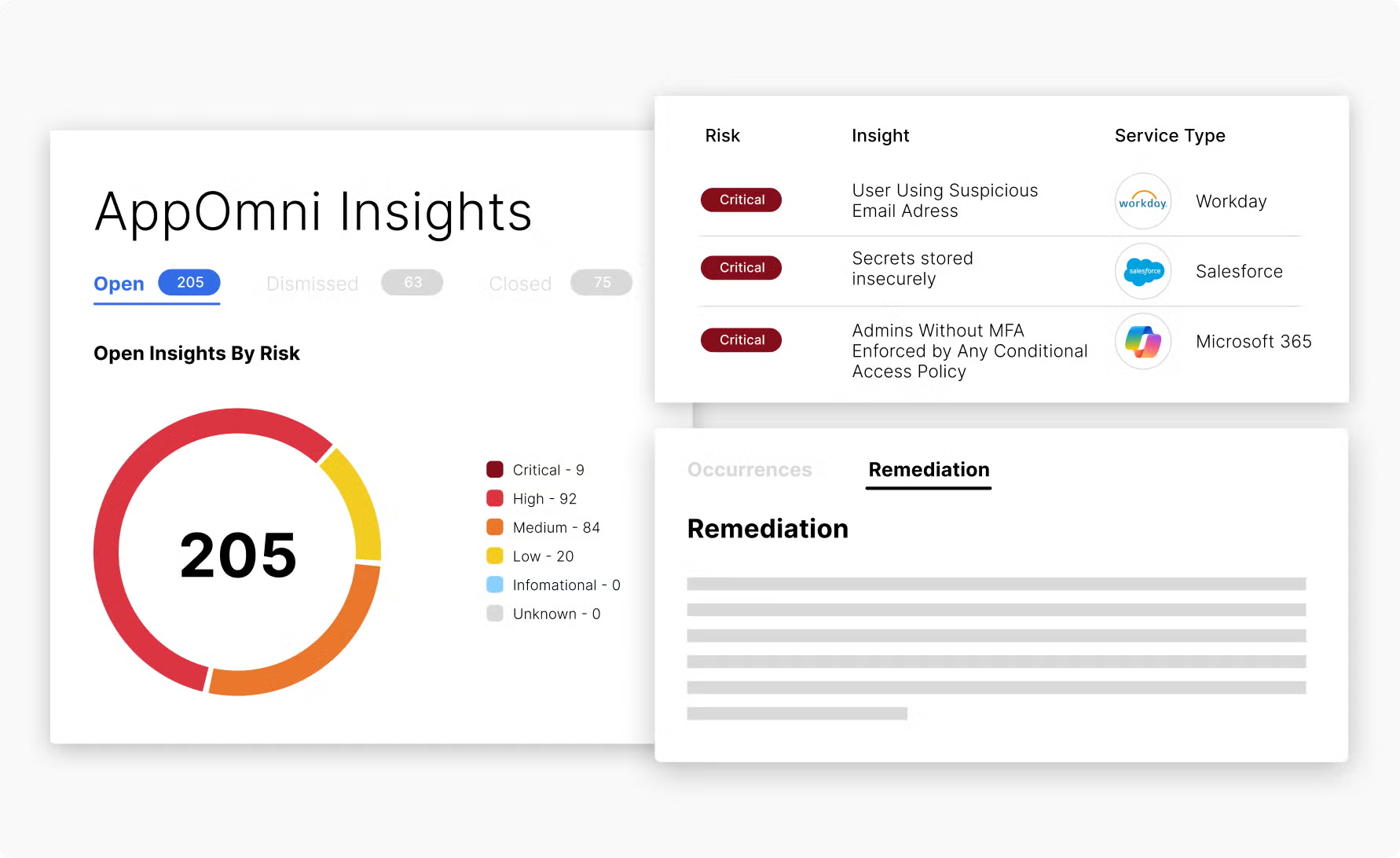
Best for: Enterprise Salesforce and ServiceNow environments
AppOmni offers SaaS security posture management with particular depth in Salesforce environments. The platform provides configuration monitoring and compliance controls for organizations heavily invested in specific enterprise applications.
Capabilities:
Limitations to consider:
AppOmni works well for organizations whose SaaS security concerns center almost entirely on Salesforce. For broader coverage, most teams need additional tools.

Best for: Data loss prevention in collaboration apps
DoControl positions itself as a SaaS security platform focused on data access governance and DLP capabilities, particularly for Google Workspace, Microsoft 365, Slack, and similar collaboration tools.
Capabilities:
Limitations to consider:
DoControl may suit organizations with specific data loss concerns in collaboration tools, but it's not a comprehensive Adaptive Shield replacement.
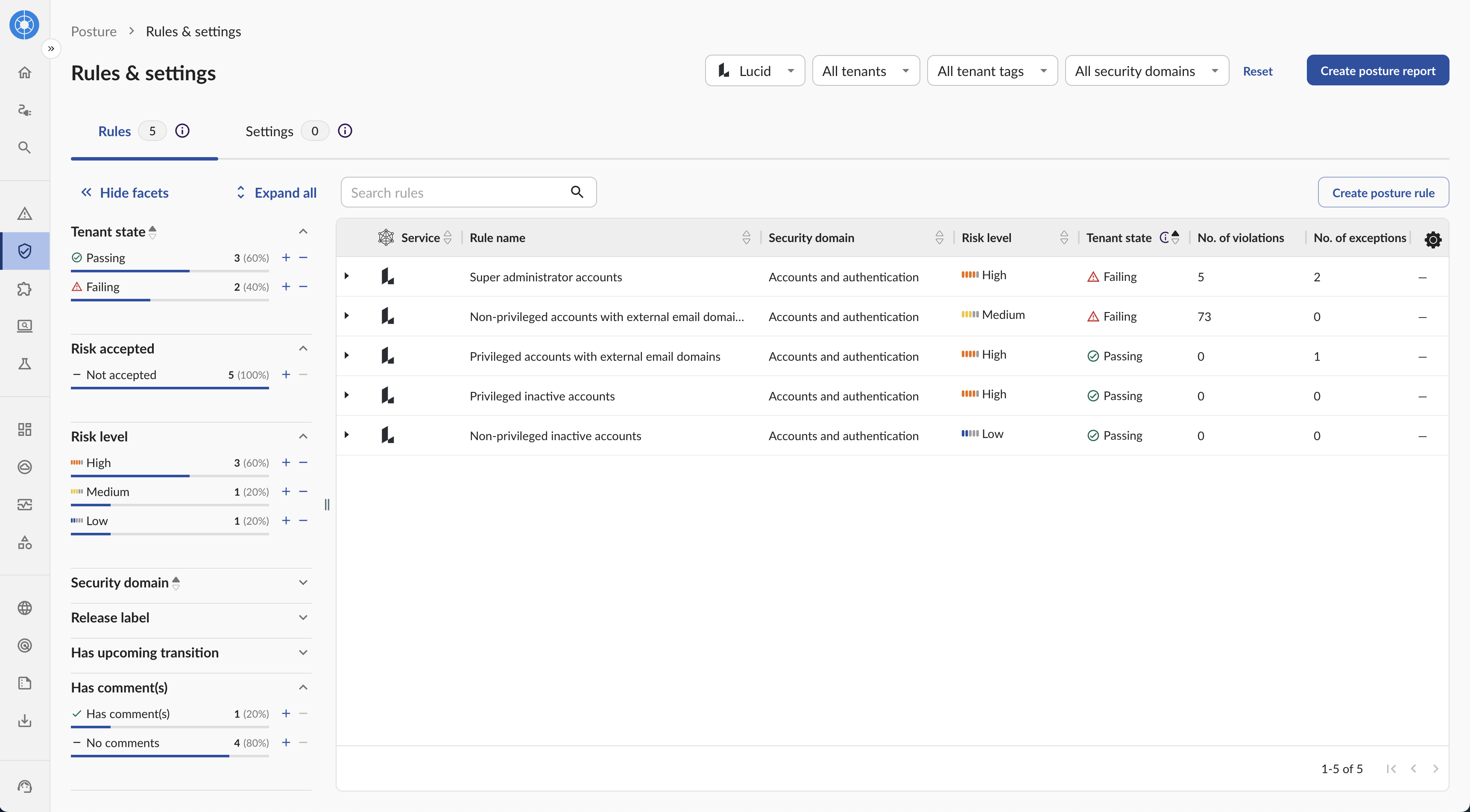
Best for: User behavior analytics and insider threat focus
Obsidian merges SSPM with User and Entity Behavior Analytics, positioning itself as a security intelligence layer for detecting insider threats and compromised accounts.
Capabilities:
Limitations to consider:
Obsidian works best as a complement to other tools rather than a standalone SSPM solution.

Best for: Organizations wanting a free tier to start
Wing Security offers a freemium model that provides basic SaaS inventory visibility at no cost, with paid tiers adding security controls and compliance capabilities.
Capabilities:
Limitations to consider:
Wing works as an entry point for organizations new to SSPM, but most outgrow it quickly.

Best for: Organizations already using Netskope's security platform
Netskope offers SSPM as part of its broader Security Service Edge (SSE) platform, providing SaaS configuration monitoring alongside CASB, DLP, and zero-trust capabilities.
Capabilities:
Limitations to consider:
Netskope SSPM makes sense only for organizations committed to Netskope's full security stack.
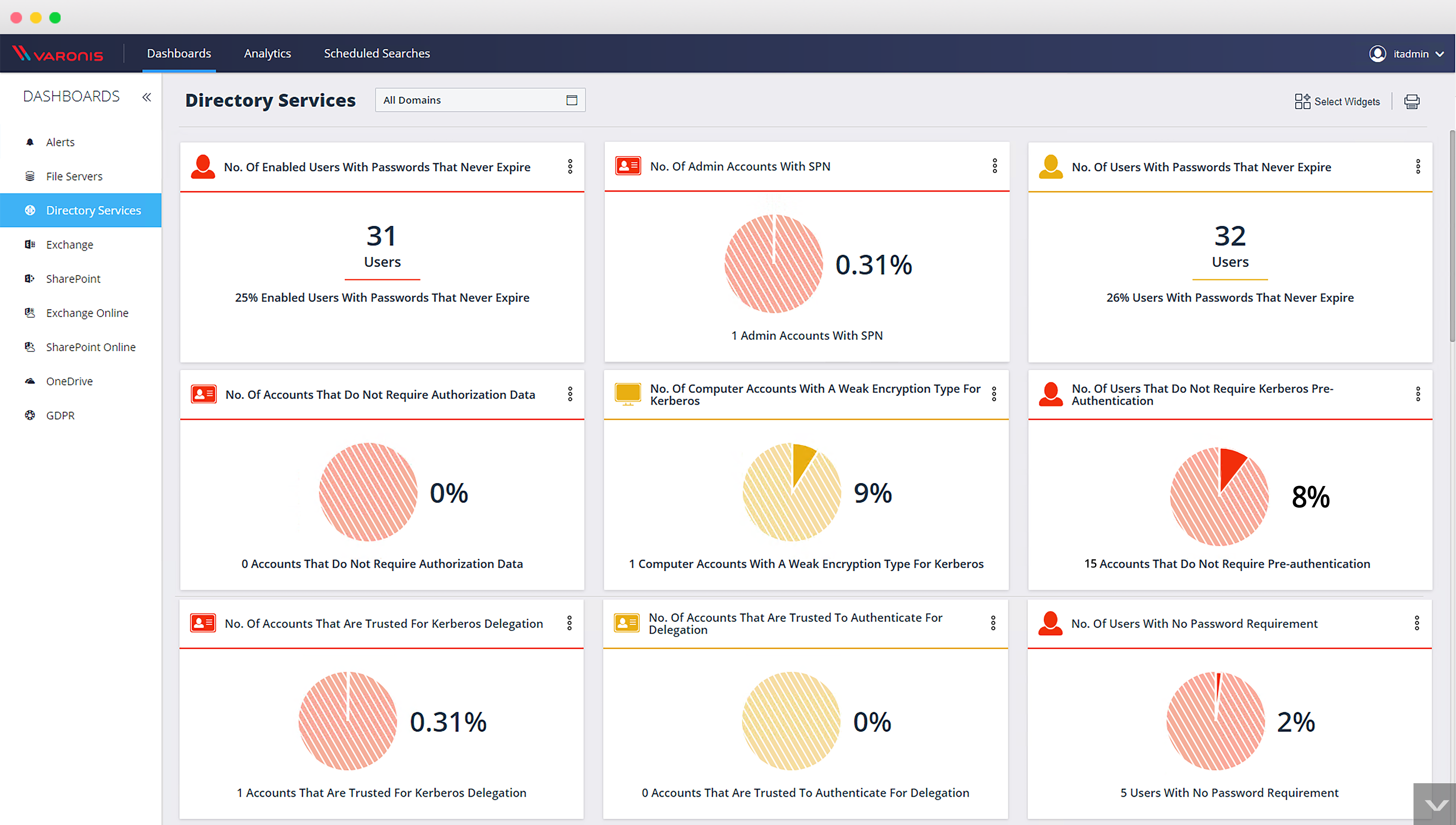
Best for: On-premises and hybrid data security
Varonis provides data security across on-premises and cloud environments, with SSPM capabilities added to its traditional data protection focus.
Capabilities:
Limitations to consider:
Varonis suits organizations with significant on-premises data security needs who want a single vendor. For SaaS-first organizations, purpose-built SSPM tools deliver better results.

Best for: Zscaler Zero Trust Exchange customers
Zscaler includes "advanced SSPM" as part of its Zero Trust Exchange platform, offering SaaS configuration monitoring for organizations already invested in Zscaler's ecosystem.
Capabilities:
Limitations to consider:
Like Netskope, Zscaler SSPM only makes sense for existing Zscaler customers.
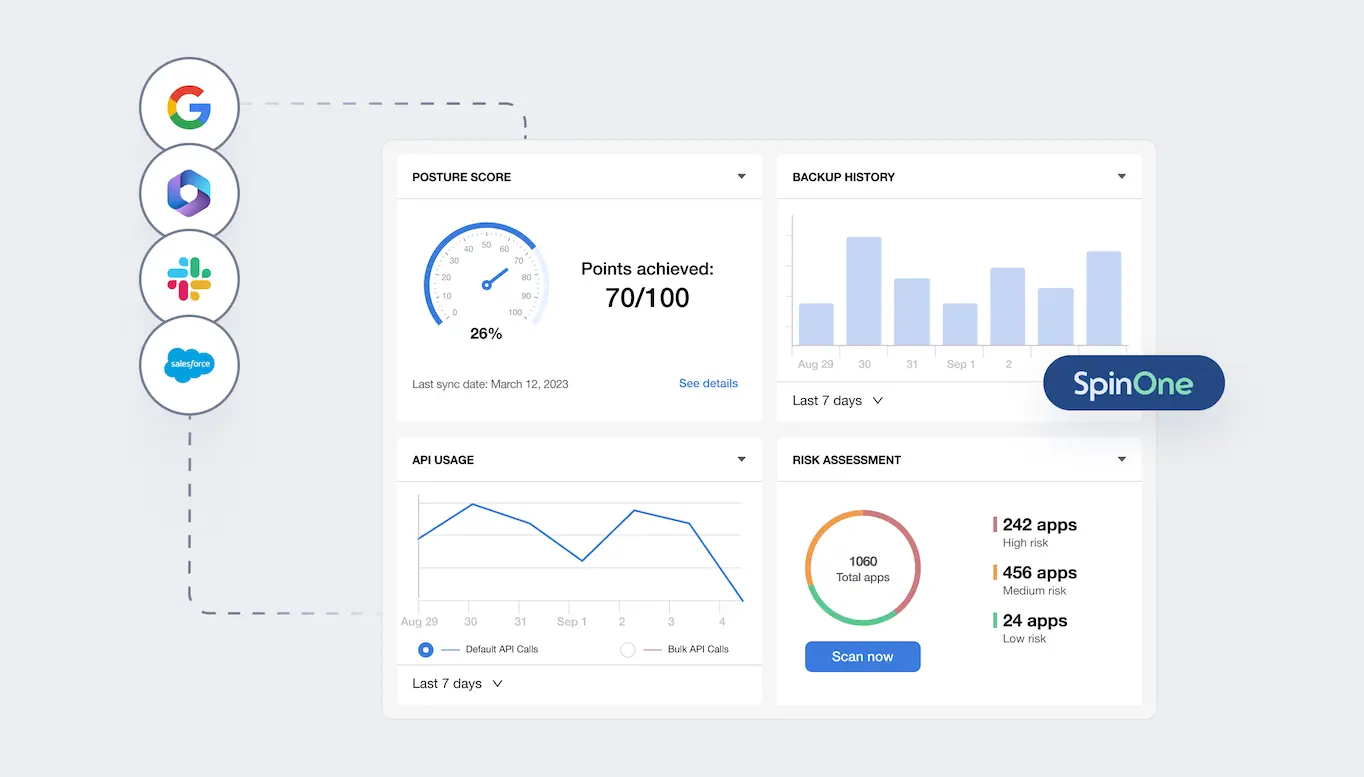
Best for: Google Workspace and Microsoft 365 backup with basic security
SpinOne combines SaaS security with backup and recovery capabilities, targeting organizations that need both functions in a single platform.
Capabilities:
Limitations to consider:
SpinOne works for smaller organizations wanting backup and basic security in one tool, but it's not a comprehensive Adaptive Shield replacement.
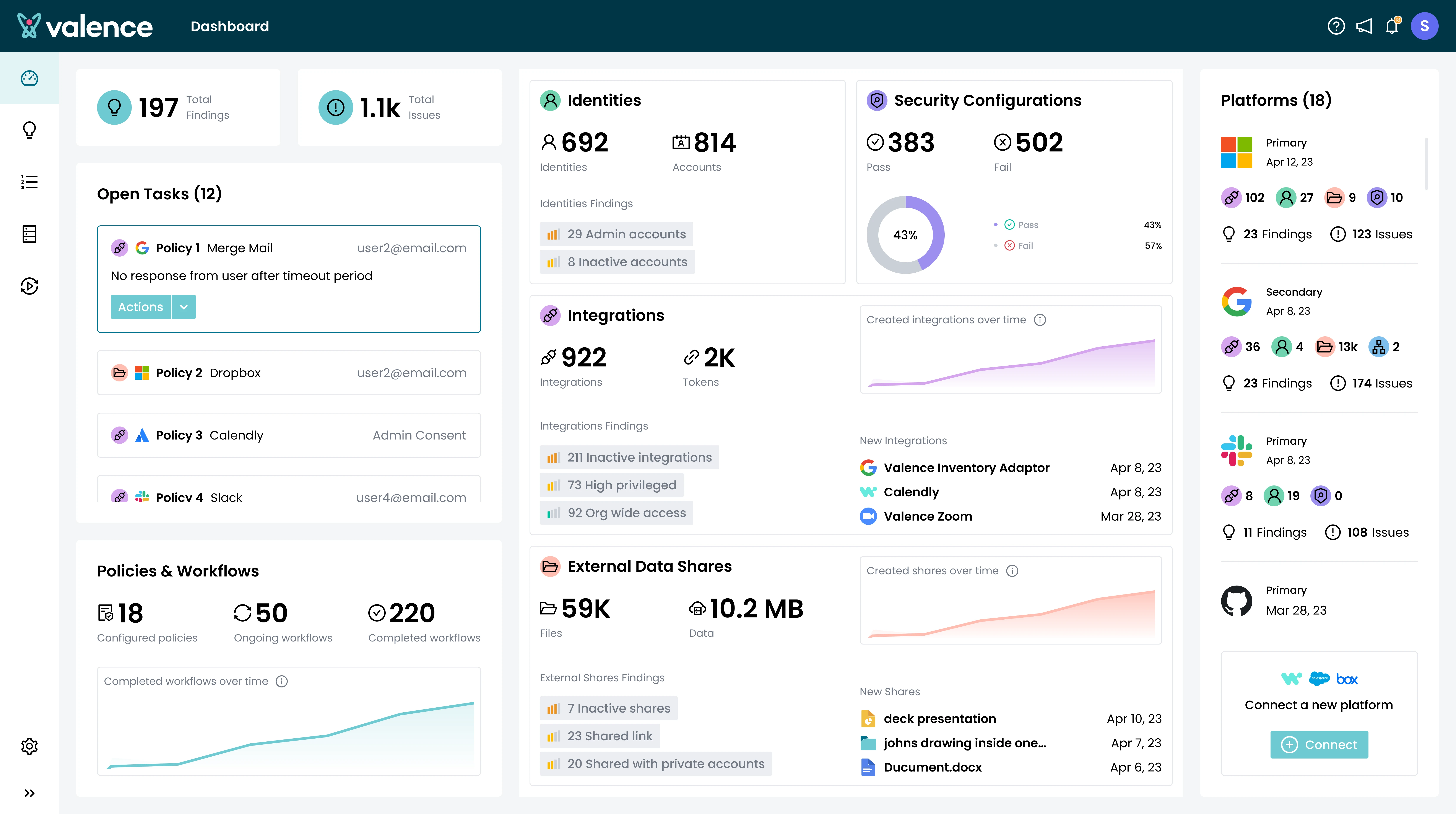
Best for: Microsoft-heavy environments
Valence offers SaaS discovery and security posture management with particular strength in Microsoft ecosystem protection.
Capabilities:
Limitations to consider:
Valence may suit Microsoft-dominated environments, but organizations with diverse SaaS stacks need broader coverage.
When selecting an Adaptive Shield replacement, ask these questions:
Adaptive Shield delivered solid misconfiguration detection, but the CrowdStrike acquisition, manual remediation model, and opaque pricing have pushed many organizations to explore alternatives.
For most security teams, Perimeters offers the clearest path forward: transparent pricing at $3/user/month, full visibility in minutes instead of weeks, and automated remediation that actually resolves issues instead of just flagging them. While enterprise SSPM vendors require sales calls, lengthy implementations, and ongoing manual effort, Perimeters delivers comprehensive SaaS security that a lean team can manage in 30 minutes per week.
The other alternatives each serve specific niches - Obsidian for behavior analytics, DoControl for collaboration DLP, platform-bundled options for existing customers - but none match Perimeters' combination of speed, simplicity, and value.
Ready to see what Perimeters can do for your organization?
Start your free trial and get complete visibility into your SaaS security posture in minutes - not weeks.
